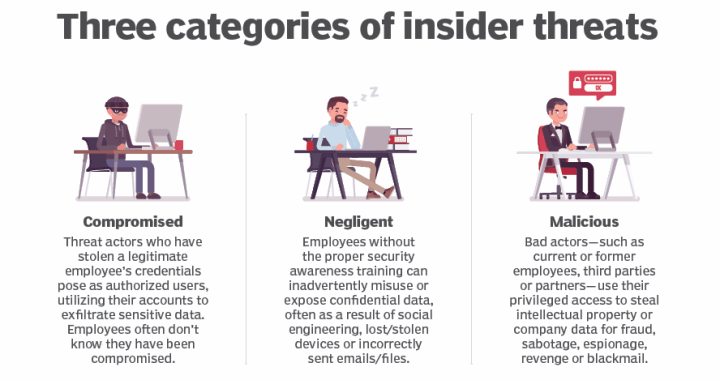
In the realm of cybersecurity, the risk of insider threats, encompassing both compromised and negligent employees as well as those who intentionally go rogue, is a critical and often overlooked aspect.
The most recent Verizon Business Data Breach Investigations Report accentuates this point, revealing that 82% of breaches involve the human element, and the severity of these attacks, including ransomware, is escalating. This underlines the assertion that people are often the weakest link in cybersecurity defenses. The challenge here lies not only in the awareness of cybersecurity threats but also in the translation of this awareness into proactive behavior. The “knowledge-intention-behavior gap” is a significant hurdle; employees might be aware of risks but fail to take necessary actions to mitigate them.
Addressing this gap requires a multifaceted approach. Effective cybersecurity programs need to account for human nature, as cybercriminals expertly manipulate human emotions such as curiosity, impulsiveness, ambition, and empathy to orchestrate breaches. To fortify the human element in cybersecurity, continuous training in communication, behavior, and culture management is essential. This involves understanding and connecting with the audience on an emotional level, closing the gap between knowledge and action, and fostering a security-conscious culture within the organization.
Moreover, technological solutions like Endpoint Privilege Management (EPM) and phishing simulations play a vital role. EPMs help manage user privileges and control application access, reducing the risk of breaches. Phishing simulations, on the other hand, are crucial for identifying vulnerabilities in the human element and educating users, thus strengthening security defenses.
The detection of insider breaches is inherently challenging due to their nature. Insiders already have access to the organization’s systems and information, making their malicious activities more difficult to distinguish from legitimate actions. This necessitates increased vigilance and a layered approach to security, combining technological solutions, robust policies, and continuous employee education and monitoring.
In conclusion, while there are no foolproof solutions in cybersecurity, a comprehensive strategy that includes safeguarding the human element is critical. Investing in robust security measures and employee training can elevate the effort required for a successful attack, thereby deterring potential attackers. Organizations perceived as more vulnerable are often targeted by cybercriminals, so enhancing security can act as a strong deterrent. This investment in cybersecurity is not just about protecting data and systems; it’s a crucial step in safeguarding an organization’s reputation, financial stability, and trustworthiness.