Think of it this way: you wouldn’t build a house without blueprints, right? You wouldn’t just start nailing boards together hoping for the best. Similarly, you shouldn’t operate your business’s digital assets without a plan for what happens when something inevitably goes wrong in the cyber world. An Incident Response Plan (or IRP for short) is your blueprint for handling a security breach or cyberattack.
The Power of AI: Beyond Automation
A force multiplier leverages technology to enhance the capabilities and efficiency of human resources. In business terms, this translates to using AI not to eliminate jobs but to free employees from mundane tasks, allowing them to focus on innovation, customer engagement, and complex problem-solving. Three key AI technologies—Large Language Models (LLMs), automation tools, and advanced analytics—are driving this shift.
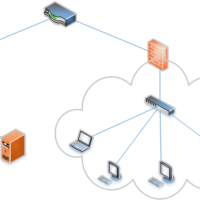
The Importance of Network Segmentation
Network security has become a top priority for businesses and organizations of all sizes, and rightfully so. Improperly configured or secured networks can create a playground for malicious hackers and automated attacks.
The Envescent Cybersecurity Workshop for 2024
Learn about the latest threats that businesses face in 2024 through our free Cybersecurity Workshop. This comprehensive webinar covers the changes happening in attacks such as ransomware, phishing, how AI is being weaponized, hacking activities by nation states such as China and much more.
The Importance of Periodic Cybersecurity Assessments
Cybersecurity is a critical aspect of modern business operations, with cyber threats evolving rapidly and becoming more sophisticated. Regular cybersecurity assessments are essential to ensure that systems, networks, cloud presence, personnel, and IT policies remain secure and up-to-date. These assessments go beyond the scope of ongoing IT Managed Services Provider (MSP) support and conventional protection measures such as anti-virus software and spam filtering.