Microsoft engineers recently presented research at the RSA security conference indicating that 99.9% of compromised accounts aren’t using multi-factor authentication (MFA). This statistic alone illustrates the enormous potential for MFA to mitigate account breaches when passwords are either guessed or exfiltrated.
The same research indicated that about 0.5% of all accounts are compromised on a monthly basis, with approximately 1.2 million such accounts compromised in January of 2020. In that same January, 2020 data set, Microsoft claimed that only 11% of the accounts had MFA configured.
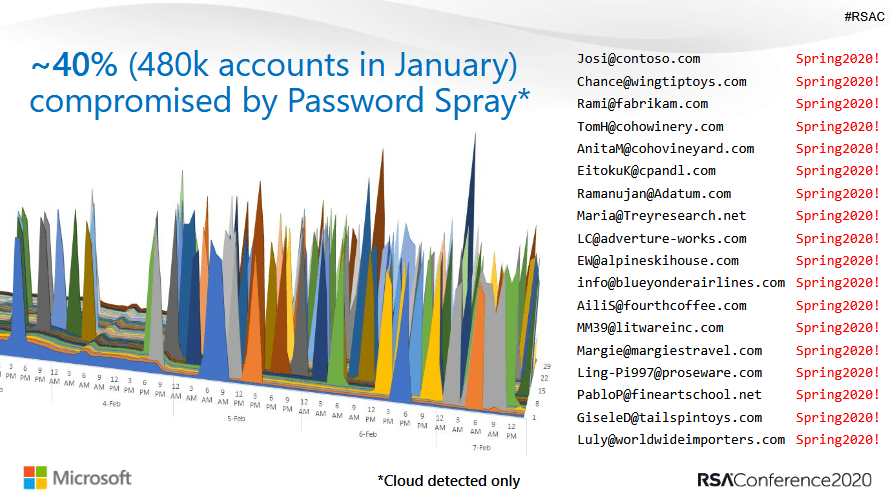
The leading cause of account compromise were password spraying, or what are commonly called brute force attacks, whereas multiple account passwords are guessed in rapid succession, using techniques that focus on the most commonly used passwords. Second to password spraying, were password replays, which involve re-using previously leaked or breached credentials. Thus re-using a username and/or password is also quite problematic for account security.
“We know that 60% of users reuse passwords. It’s super common,” said Lee Walker, Identity and Security Architect at Microsoft.
The resounding recommendation was enabling MFA across all accounts where it could be utilized. A recommendation that our security experts at Envescent strongly agree with as it is a powerful account risk mitigation strategy, reducing the potential for account breaches by up to 99.9%.

