Expert Assessment of Your Exploitable Attack Surface
Network and system vulnerability audits show what resources may be exploitable. Penetration tests demonstrate whether that attack surface can actually be exploited. The results are beneficial for compliance and having a better handle of the actual attack surface exposed to exploitation.
The Evolving Threat Landscape: Why Penetration Testing is Non-Negotiable
Cyber threats are constantly evolving, becoming more sophisticated and targeted. Relying solely on automated scans or basic security measures is no longer sufficient. Why? Because attackers are persistent and creative. Penetration testing bridges the gap between theoretical security and real-world risk by:
- Identifying Hidden Weaknesses: Automated tools often miss complex vulnerabilities, misconfigurations, or logical flaws that human testers can uncover.
- Testing Defenses Effectively: Verifies if your firewalls, intrusion detection systems, and other security controls can actually stop a determined attacker.
- Validating Security Investments: Ensures the money and effort spent on security measures are providing tangible protection.
- Going Beyond Compliance: While often required for regulations (PCI-DSS, HIPAA, etc.), pen testing goes further by assessing the actual risk, not just checking a box.
- Understanding Attacker Motivation: Simulates attacks based on common threat actor tactics, techniques, and procedures (TTPs).
Ignoring penetration testing leaves your organization exposed to potentially devastating breaches, financial loss, reputational damage, and legal liability.
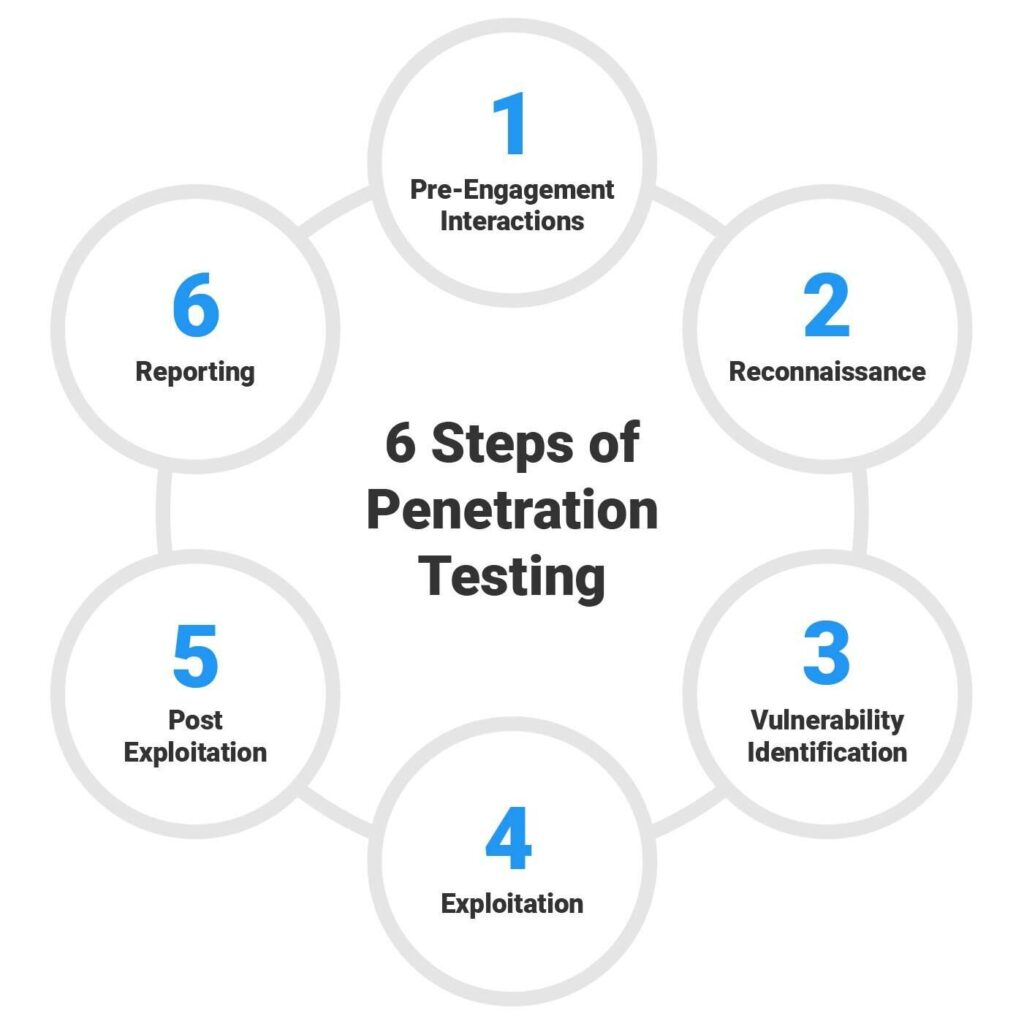
Our Penetration Testing Services
We offer a full spectrum of penetration testing services tailored to your unique environment and risk profile:
Network Infrastructure Penetration Testing:
- Assessing firewalls, routers, switches, and other network devices for misconfigurations and vulnerabilities.
- Testing network segmentation and access controls.
- Identifying open ports, services, and potential entry points.
Web Application Penetration Testing:
- Deep analysis of web applications for common vulnerabilities (OWASP Top 10 like SQL injection, XSS, CSRF, etc.).
- Testing authentication, authorization, session management, and input validation.
- Evaluating API security.
Mobile Application Penetration Testing (iOS & Android):
- Assessing the security of native and hybrid mobile apps.
- Testing client-side logic, data storage, communication channels, and backend integrations.
- Evaluating platform-specific vulnerabilities.
Cloud Infrastructure Penetration Testing:
- Assessing security configurations in cloud environments (AWS, Azure, GCP, etc.).
- Evaluating identity and access management (IAM), storage security, and network settings.
- Testing for common cloud-specific misconfigurations.
Wireless Network Penetration Testing:
- Assessing Wi-Fi network security (WPA2/WPA3, captive portals).
- Testing for rogue access points and vulnerabilities in wireless protocols.
Social Engineering Testing:
- Simulating phishing attacks, vishing (voice phishing), baiting, and physical security tests to assess human vulnerability.
- Evaluating employee awareness and response procedures.
Physical Security Testing:
- Assessing the effectiveness of physical security controls like access controls, surveillance, and building security.
Red Team Engagements:
- A highly realistic simulation of a full-scale attack, mimicking sophisticated adversaries.
- Involves multiple phases: reconnaissance, initial compromise, lateral movement, privilege escalation, data exfiltration, and post-exploitation.
- Tests the entire security posture, including people, processes, and technology.
Why Choose Us?
- Experienced & Certified Experts: Our penetration testers are highly skilled professionals holding industry-leading certifications (e.g., OSCP, OSCE, CRTP, GPEN, CISM).
- Customized Approach: We understand every organization is unique. We tailor our testing scope, methodology, and tools to your specific risks and objectives.
- Realistic Simulations: We don’t just tick boxes; we simulate real-world attacker behavior using proven methodologies (like PTES, MITRE ATT&CK) and creative thinking.
- Comprehensive Reporting: We provide detailed, actionable reports that clearly articulate findings, potential impact, risk ratings, and prioritized remediation steps.
- Clear Communication: We maintain transparent communication throughout the engagement, keeping you informed and involved.
- Global Reach & Local Expertise: We serve clients worldwide while bringing deep local knowledge where needed.
- Confidentiality & Integrity: We adhere to strict ethical standards and non-disclosure agreements, protecting your sensitive information.
Receive Expert Help from Security Professionals

Envescent provides comprehensive penetration testing services for small, medium and large businesses around the world, including our neighbors in Virginia, Maryland and Washington, DC.
We utilize cutting edge techniques and our proprietary white hat hacking capabilities to provide the most accurate and complete results possible.
Our experts will work closely with your team to identify soft spots in your security and determine if they are able to be penetrated for privilege escalation, data exfiltration, denial of service attacks and more. Knowing your network and systems true attack surface allows remediation to focus on the most immediate and critical threats first, ensuring effective utilization of resources. We work closely with our clients to ensure we provide the most effective solution to their security concerns and compliance requirements.
Contact us to Learn More
If you are interested in discussing our penetration testing security services please contact us. We’ll be delighted to help secure your business.
