Cybersecurity is a critical part of every business’ operational durability. Without attention to it, an attack can be crippling. We recommend business owners and managers view cybersecurity as an investment, rather than a sunk cost, as it pays in dividends of business continuity and resilience.
Risks
Small and medium-sized businesses (SMB) are often the target of attacks due to a lack of compliance, maintenance, monitoring, policy, protection, training and vulnerability management. Most SMB incorrectly believe that they aren’t the target of such attacks, thus the requisite effort to remediate these issues is not taken.

This results in a dire lack of security in cloud presence(s), data, device(s), network(s), office(s) and personnel awareness, which, when combined with the increasing scale and sophistication of attacks, makes for an untenable situation that can lead to data loss, manipulation or breach as well as denial of service (or access to valuable resources). The outcome of a successful breach or other attack may also harm business finances, employee morale, company reputation and create legal and other liabilities.
We illustrate three examples of such attacks in this post: with a technological, physical and human security breach.
Trends
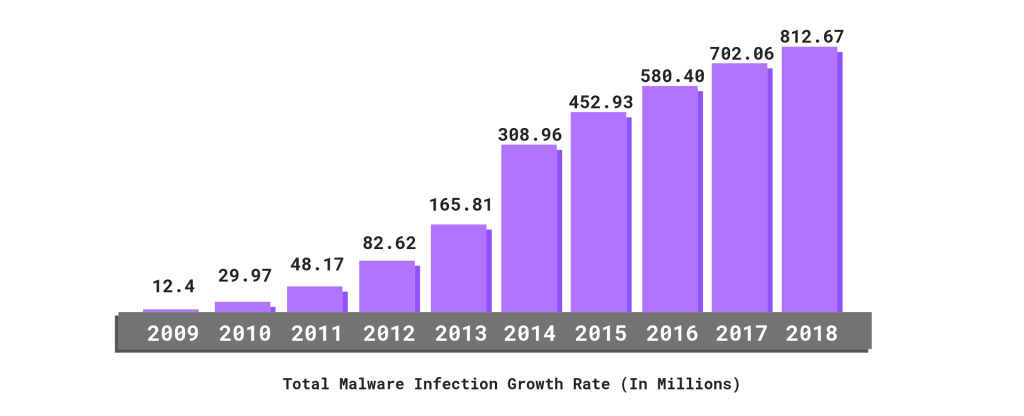
Malware and phishing attacks are on the rise, and more are being targeted against SMBs specifically as they are often seen as low hanging fruit with deeper purses than consumers. Many of these attacks are targeting data for exfiltration or to hold for ransom.
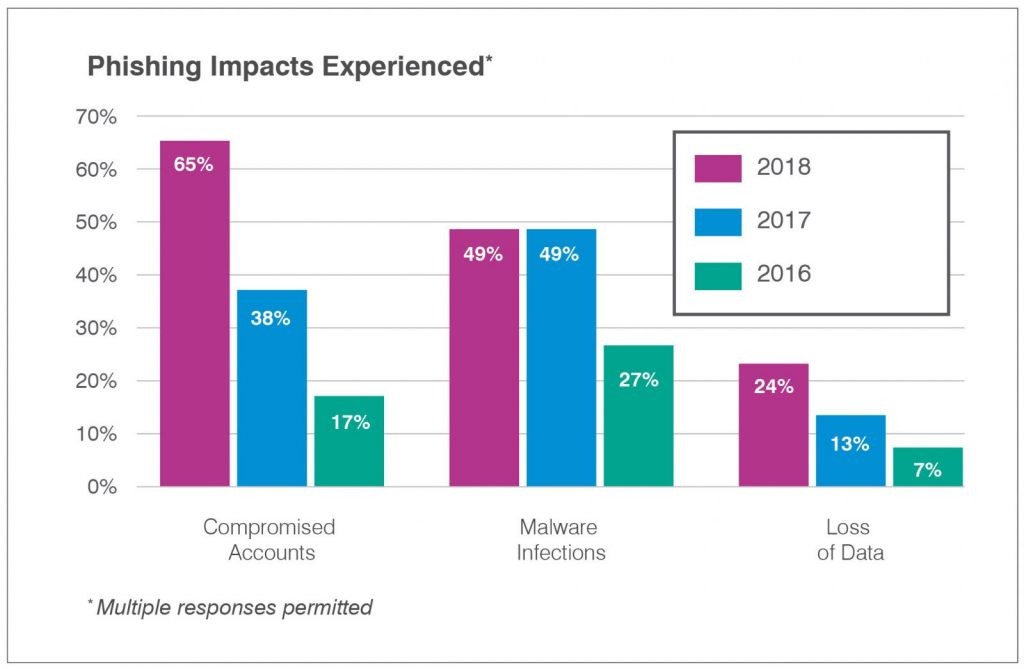
Most of these attacks that we observe would have been mitigated or even prevented with a greater focus on cybersecurity best practices.
Best practices
- Have a written IT security policy and train on it.
Your IT security policy is the foundation from which all the rest is built. And it must be trained on so that employees and contractors are aware of company expectations, regulatory requirements, etc. There are templates available from SANS to get started or you can contact Envescent for hands-on guidance.
- Patch all of your devices (phones, computers, network appliances) as updates are available.
Microsoft Windows, for example, puts out patches on the second Tuesday of every month. It’s important to install these, as well as patch your phone and every other device regularly.
- Change passwords at least twice a year.
While recommendations may vary here, we continue to recommend changing passwords regularly due to them ever increasingly being breached / leaked. Further, we recommend using unique and complex passwords for each account.
- Use secure password management: KeePass, LastPass, OnePass, etc.
Password managers help you use one password (or pass phrase) to manage all of your passwords. They will generate complex (hard to guess) passwords as well and store them in an encrypted database.
- Use two-factor authentication where possible.
A two-factor authentication application, like Authy or Google Authenticator can generate a one-time code for supported accounts to have greater security. That way if someone has your password, but not the device with the application, they cannot (easily) get in to your account.
- Endpoint protection and a network firewall.
Every business needs commercial grade endpoint protection (which is a more comprehensive anti-virus solution) as well as a network firewall to guard the network perimeter. Internet-facing devices are exposed to automated attacks up to every 10 seconds from around the world. A firewall can deter these attack attempts significantly.
- Do not open suspicious emails or attachments.
If you receive a suspicious email, even if it seems somewhat legitimate, either call the party in question, verify the email is from the party in question (examine the email header) or otherwise ensure the content can be validated before opening and interacting with it, opening attachments or links.
- Secure incoming and outgoing email traffic.
All email traffic should be secured, both coming to and from your business. There are options such as Microsoft Advanced Threat Protection for Office 365 customers as well as Proofpoint which can link in to just about any email configuration. It’s also important to have a secure framework that prevents others from using your email addresses. DMARC provides just such a framework and it is a standard that both government agencies and large companies are adopting and encouraging (or requiring) their vendors to adopt as well.
- Block advertisements in your web browser.
Digital advertising, while seemingly innocuous, can carry malicious payloads both in the ad itself as well as whatever resources it is linking you to. We recommend filtering advertising at the browser and firewall level wherever possible. Plugins such as uBlock Origin and provide that functionality. Blocking ads can also reduce data usage and improve privacy.
- Use a secure DNS service such as Quad 9.
DNS is sort of like a phone book directory of the Internet. Every time you visit a website, the IP address must be resolved. Malicious websites are documented by secure DNS providers, so that when someone attempts to visit them the DNS provider will reject the request. Thus providing an additional layer of security.
- Encrypt and secure all sensitive data and devices.
All important data and devices should be encrypted. This reduces the chance of your data being breached or leaked. Without encryption your data is much more vulnerable to exfiltration, manipulation and leakage.
- Wipe old devices before recycling.
Every old device should be wiped and have its storage physically destroyed before they are recycled. Whether it is a phone, tablet, computer, server, tape backups, etc. Many facilities will also provide a certificate of destruction which can be kept as an item of record.
- Purchase a cybersecurity insurance policy.
All businesses should have a robust cybersecurity insurance policy to shield them from the extreme liabilities that may arise if there is a successful attack. It’s just as important to fully understand such a policy. Reading every page or having an expert help. There are requirements that insurance providers set forth which need to be honored if the coverage is going to be effective and approved. Work with a broker that can help shape a policy specific to your company’s needs.
- Take engagement letters and other compliance seriously. These are binding legal obligations.
Whether your company is in a regulated industry, does business with regulated industries or has other compliance and engagement letter-based obligations, it is crucial to honor these commitments.
- Consider hiring a qualified independent security professional to help your company stay safe.
We can help! Envescent is local, founded and based in Arlington, Virginia with 20 years of cybersecurity and related technological experience. Contact us to schedule a consultation!